Kerberos Market Interface
Essential screens from our privacy-focused market
Login Portal
Enhanced security with optional 2FA and PGP verification
Registration
Optional profile creation with secure recovery phrase

Homepage
Market homepage showing balance, products, vendors, and more.
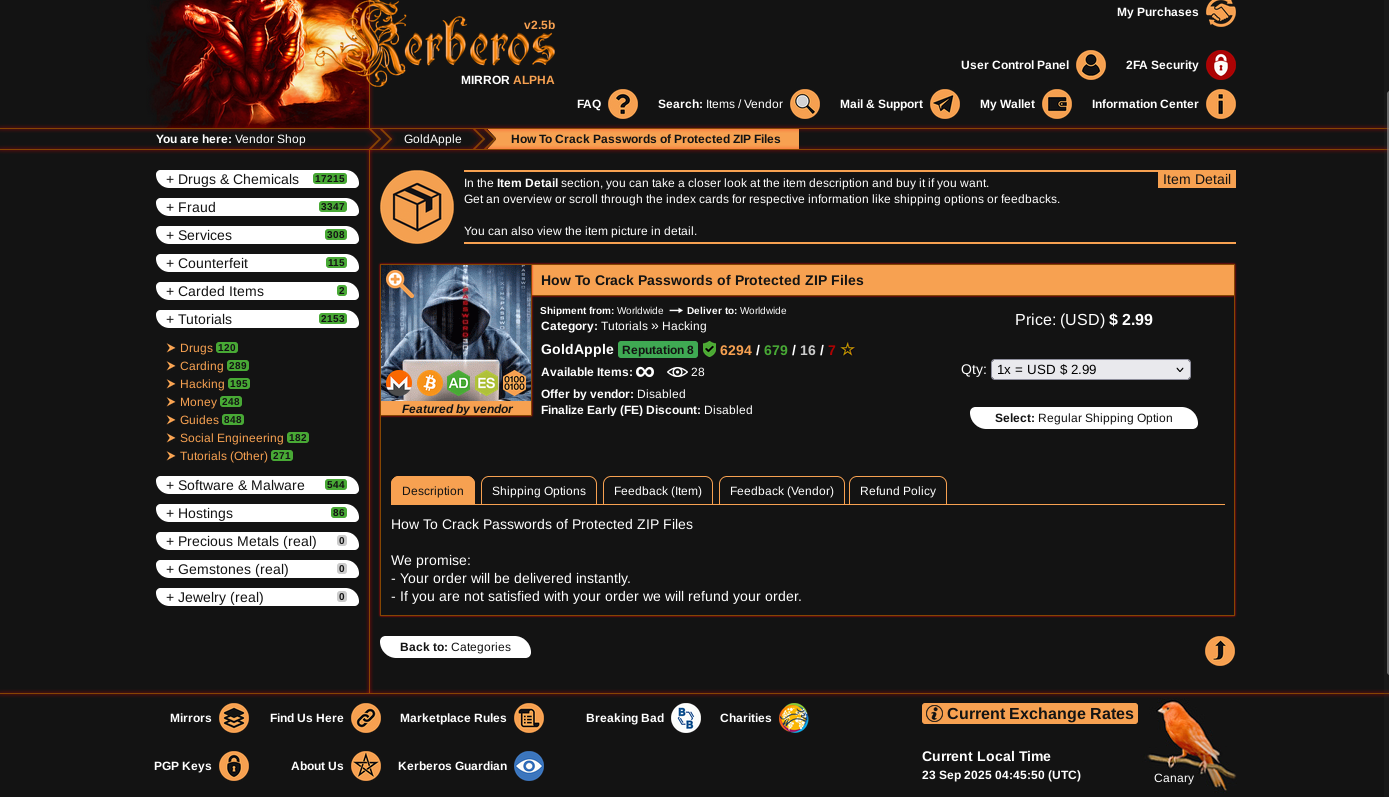
Product Listings
Intuitive interface with escrow protection and seller ratings